At Ignite 2018, Microsoft announced the preview release of AutoPilot supporting Hybrid Join. The end result of a device being that it would be joined to your Active Directory domain and also hybrid joined to Azure AD. This is explained in the session at the link below:
BRK3015 – Modern deployment with Windows Autopilot and Microsoft 365 (Part 2 of 2)
This was very exciting news and a lot of people have been waiting on this feature to arrive. Microsoft formally released their documentation for this process and released it into preview on the 2nd November 2018.
https://docs.microsoft.com/en-us/intune/windows-autopilot-hybrid
I thought I would set it up and see how it works. Lets start with the pre-requistes.
- Successfully configure hybrid Azure Active Directory join devices.
Microsoft detail in the article that your domain must have hybrid join configured and working. To ensure it was working I built a new domain in my lab, setup seamless sign on and auto hybrid join. I am not going to go into much detail about how to configure them as there are loads of articles on the web how to do this.
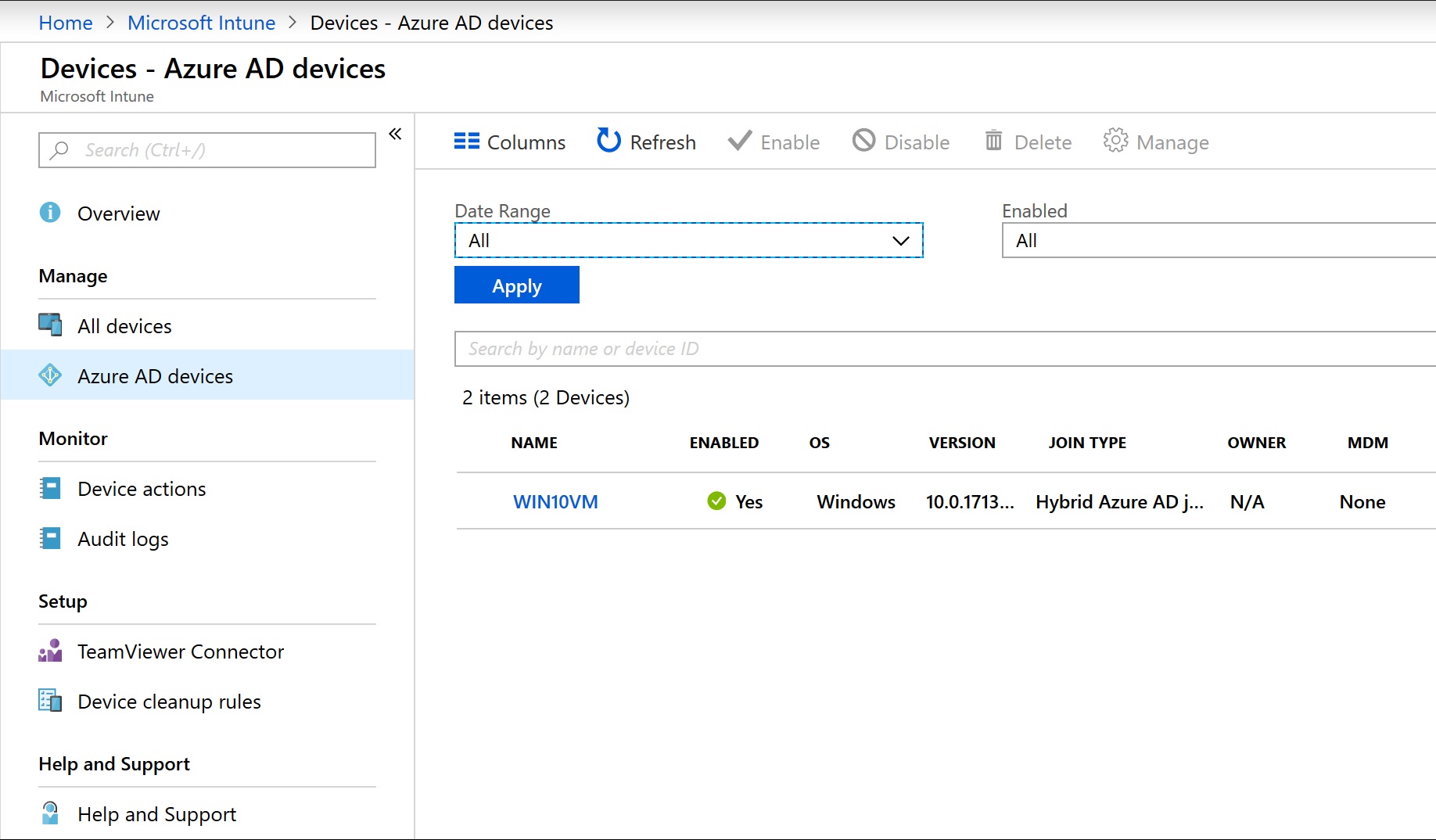
I built a new windows 10 VM just to test hybrid join was working. Running a dsregcmd /status on my machine joined to the domain I could see it hybrid joined to Azure AD. I could also see it in Azure.
The devices to be enrolled must also:
- Be running Windows 10 with the October 2018 update.
Since 1809 was recalled and not available, I changed a new Windows 10 VM to the insider program and downloaded the latest release. Taking me well past 1809.
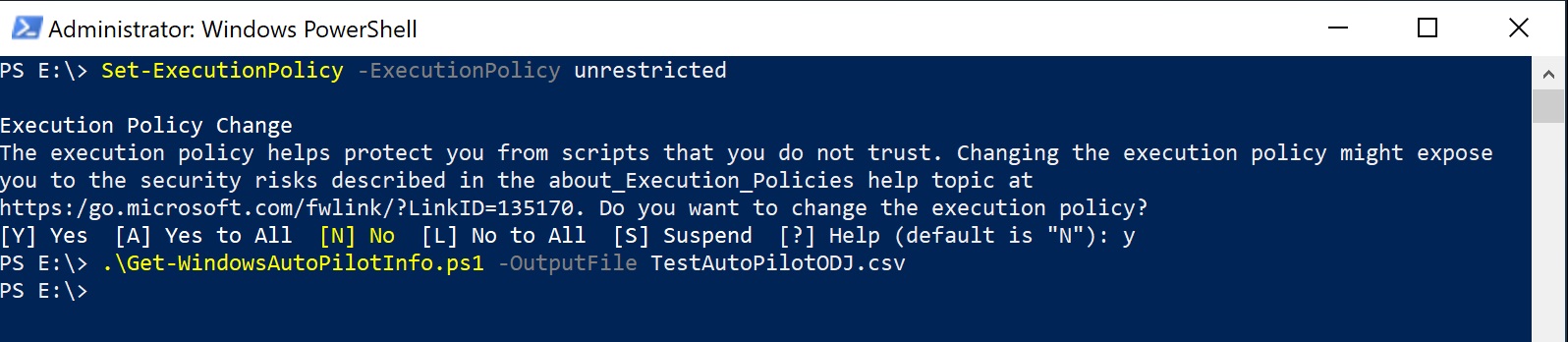
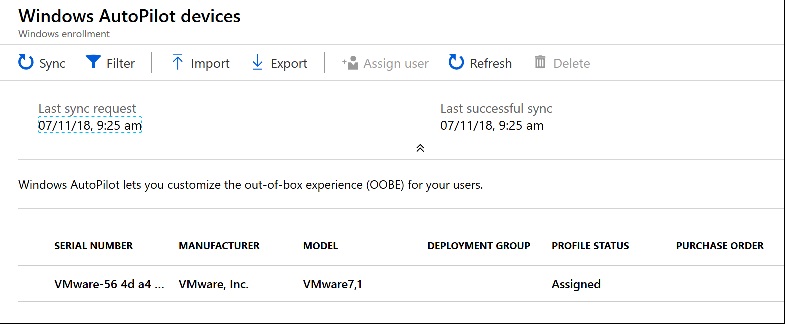
Once the VM was built, I obtained the AutoPilot Information for the device.
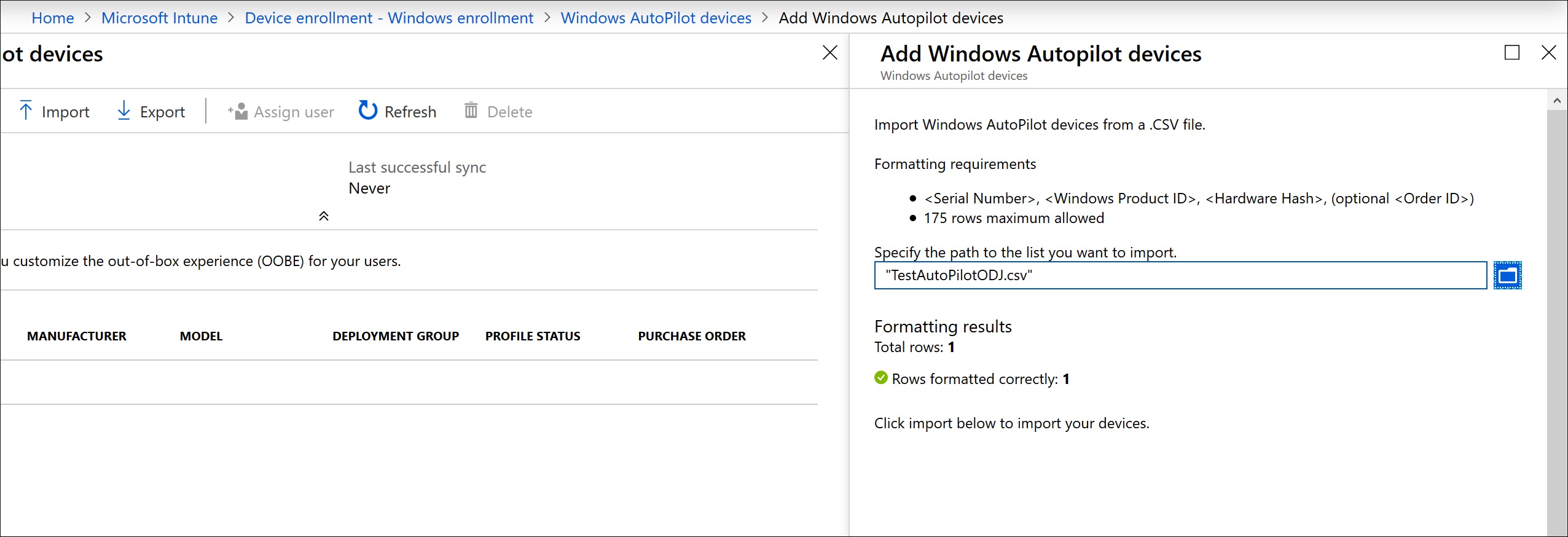
I then imported it into the AutoPilot devices. Since I know this takes ages to take effect I wanted to get this done ASAP.
- Have access to the internet.
Done!
- Have access to your Active Directory (VPN connection not supported).
I will come back to this one later on!!!!
- Go through the Out-of-Box Experience (OOBE).
I reset the device back to default to get it back to the OOBE.
With all the pre-requistes done, I could then proceed with the rest of the steps. I configured my MDM enrollment to All. I built a new server which would house the Intune connector. The server was called Intune. I created a new OU where my new AutoPilot’d devices would be created and delegated permission to this server to create and delete computer objects.
Right click on the new OU, delegate control.
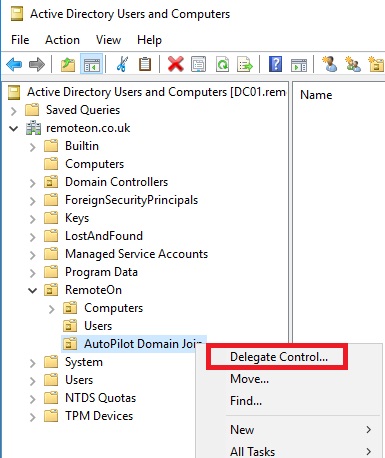
Change the object type to include computers.
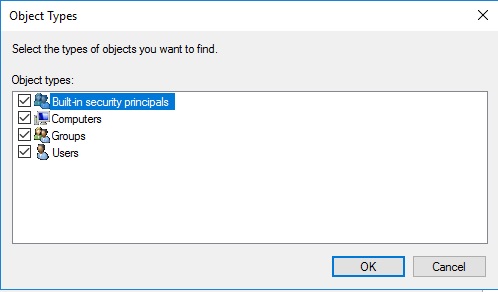
Now add the server which will have the intune connector installed on it. Mine is INTUNE.
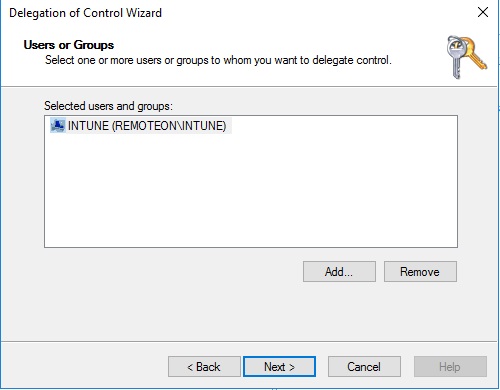
Click Create a custom task to delegate
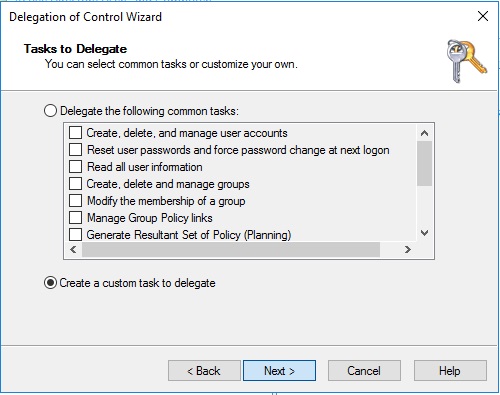
Select Computer Objects and then tick both boxes down the bottom.
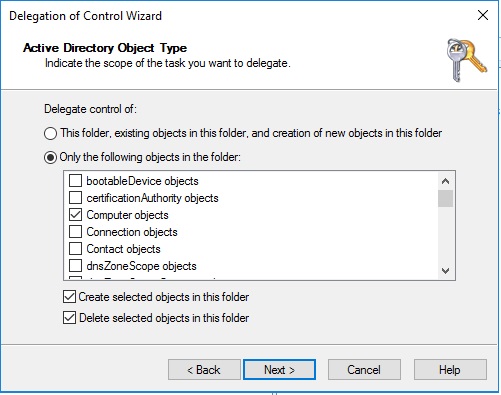
Now select full control. Click next then finish on the next screen.
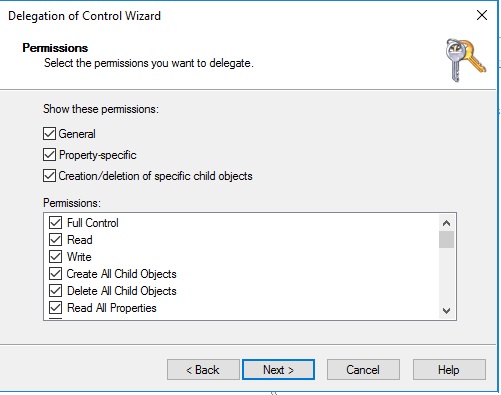
We can now proceed with the installation of the Intune Connector. Go into windows enrollment within Intune and click on Intune Connector for Active Directory.
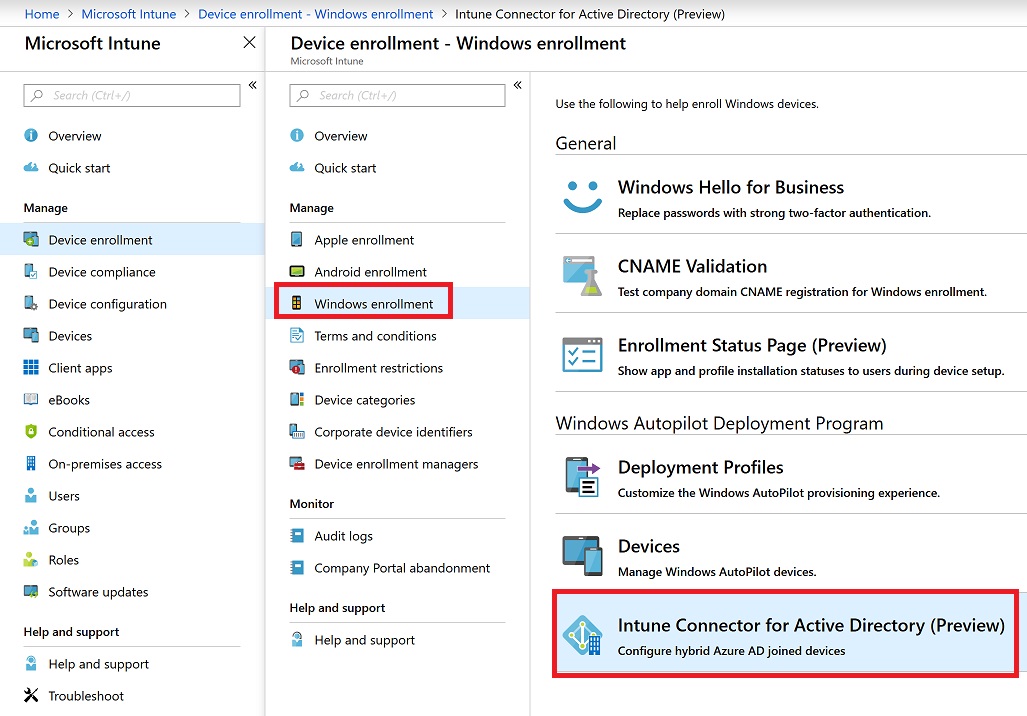
Click download connector.
If you run into an error 0x80070658 when installing, check out my article below to resolve.
Windows AutoPilot – Intune Active Directory Connector Install Error 0x80070658
Click I agree and then click Install
It whizzes through with no interaction. Click Configure now when complete.
Login to your 365 tenant.
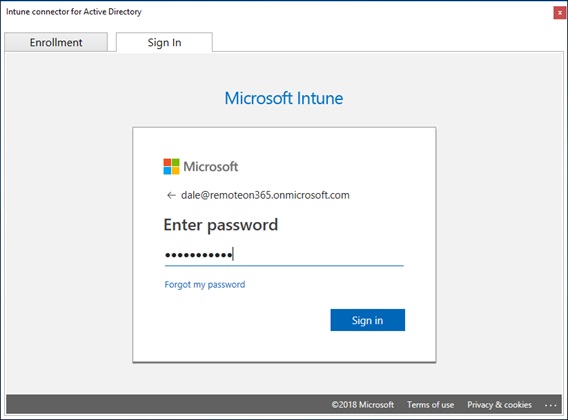
Once the connector is registered you will see it within the Intune Connectors option in the Intune Portal.
We have already registered a device within AutoPilot. I created a new Azure AD group with my device in it and then started to create the AutoPilot Deployment profile. Be sure to select Hybrid Azure AD Joined
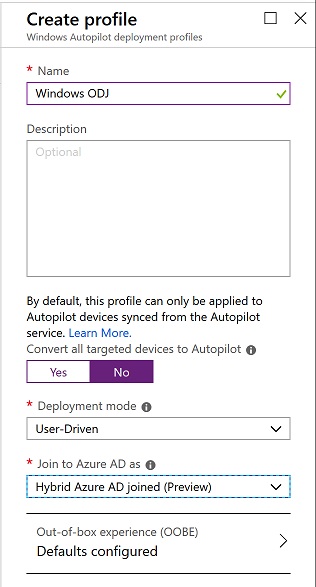
I then selected the OOBE experience I wanted. I selected administrator so I could log into the device after and make changes.
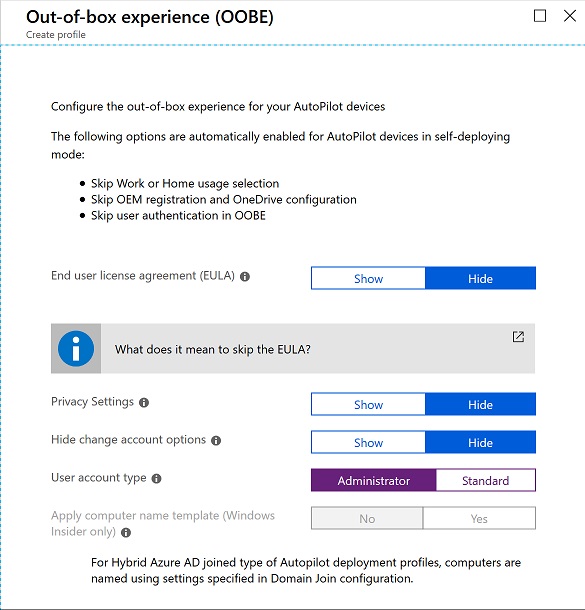
I then assigned this deployment profile to my device group.
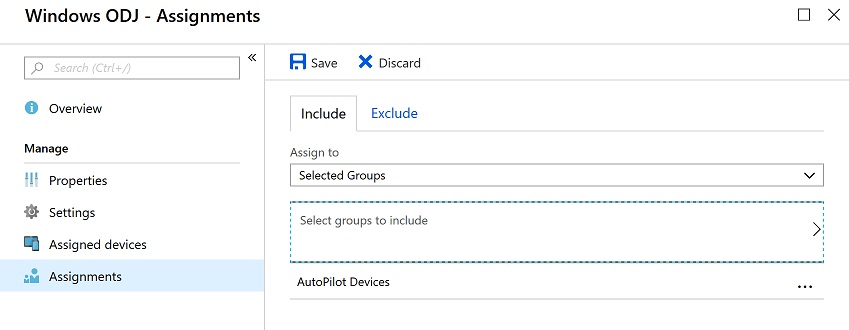
I created an enrollment policy to.
I then created a new Domain Join Configuration policy in Intune.
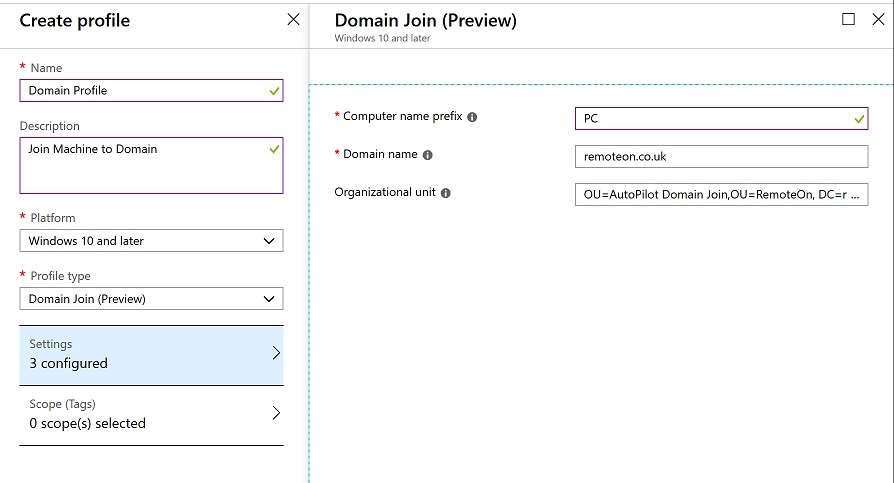
The value for my OU was:
OU=AutoPilot Domain Join,OU=RemoteOn, DC=remoteon, DC=co, DC=uk
Once created this configuration policy was then assigned to the same device group.
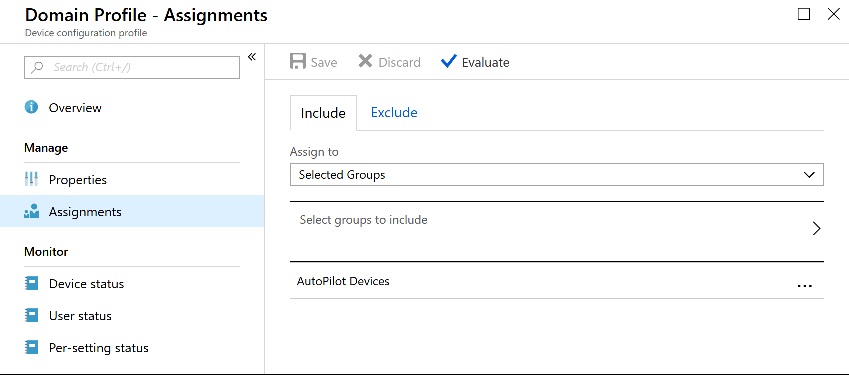
Before I reset my test autopilot VM, I wanted to make sure that the AutoPilot profile had been assigned properly. I could see that it had.
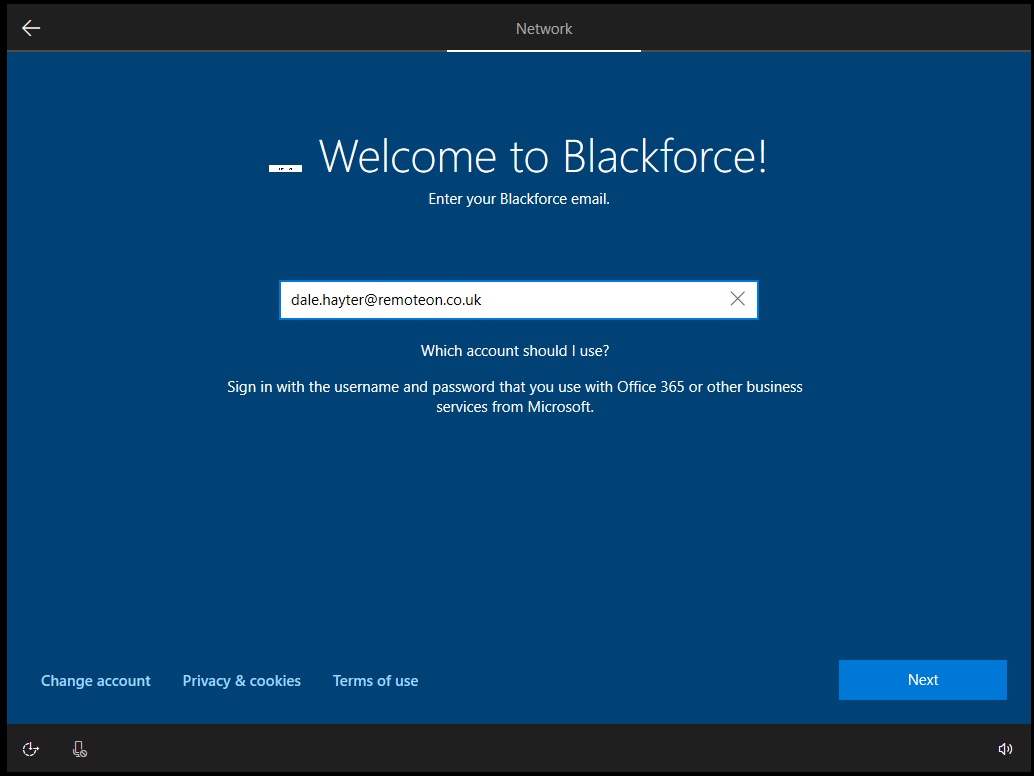
I was now good to reset my AutoPilot device. I was then greeted by the AutoPilot login screen complete with my Azure AD branding. I logged in with my credentials
It then started doing the AutoPilot process.
It rebooted twice.
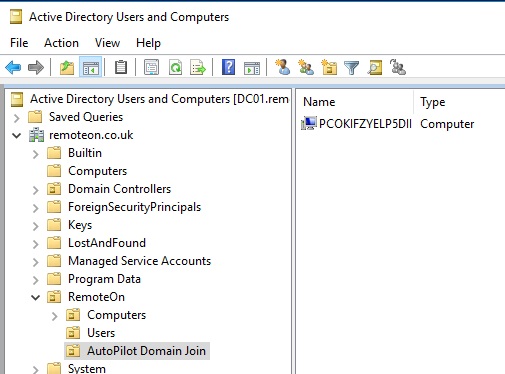
I kept an eye on my Active Directory OU during the process. My new machine appeared in my OU so I knew the process was working.
After a while I was left with a machine waiting for my AD login credentials.
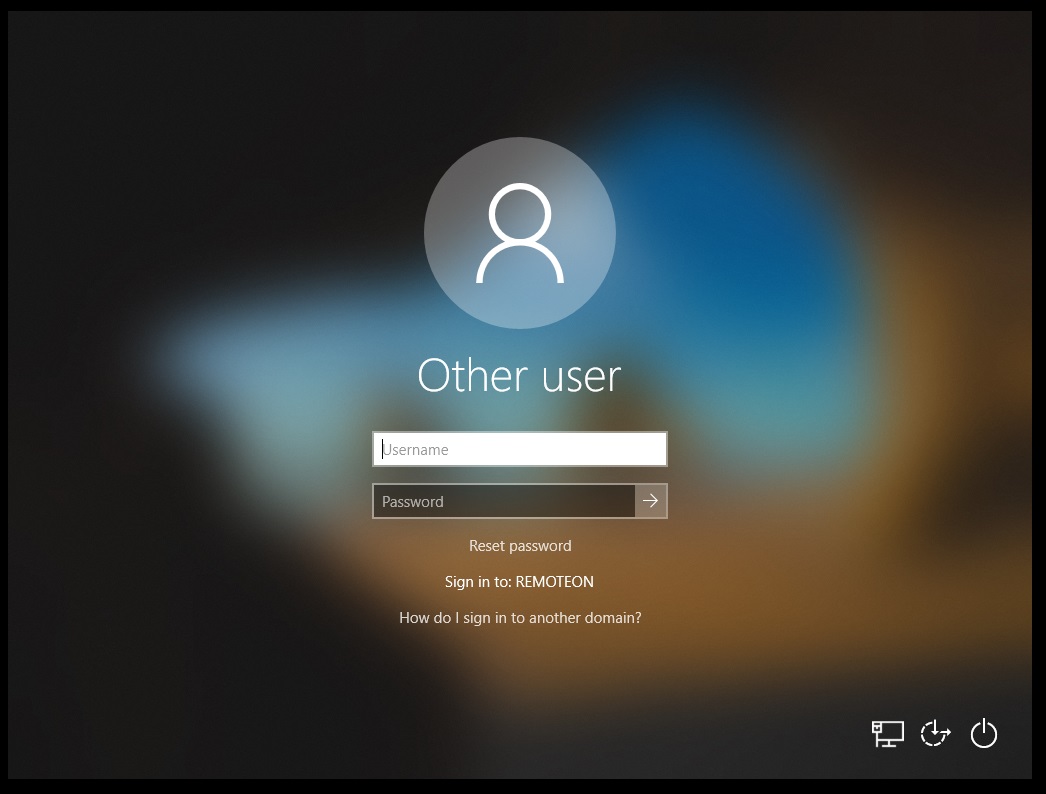
My machine at this time did not have access to the Domain across the LAN. I was simulating the device being remote. I couldnt login as the domain was unavailable.
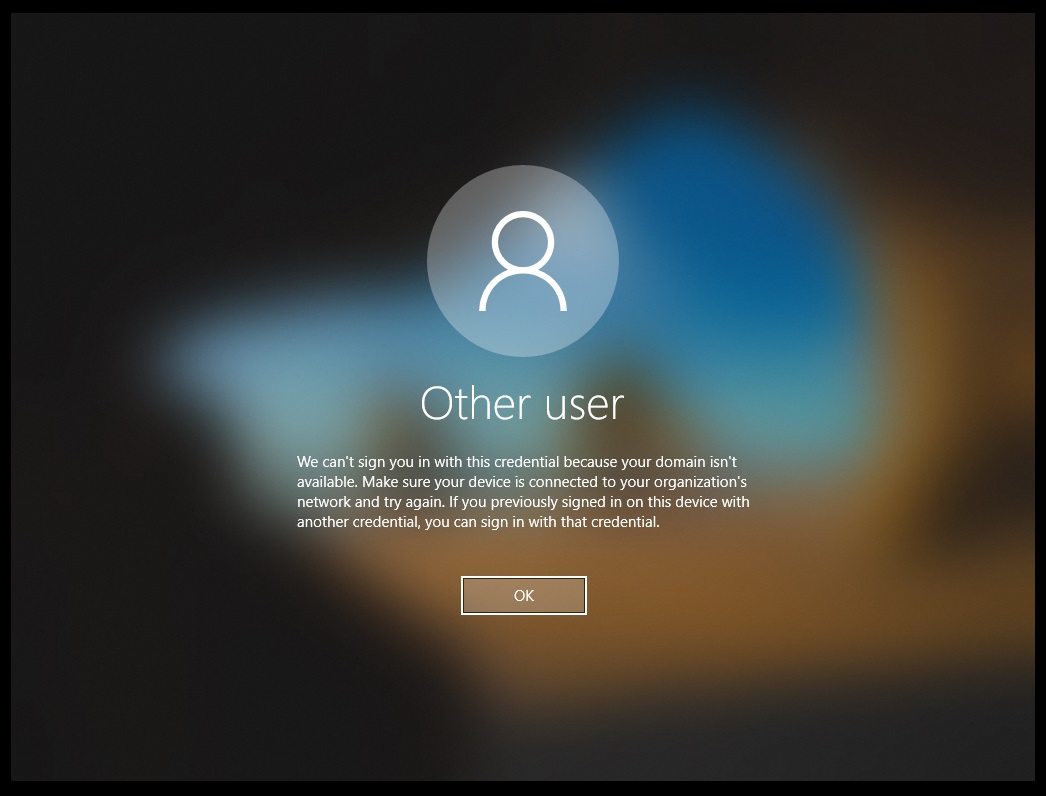
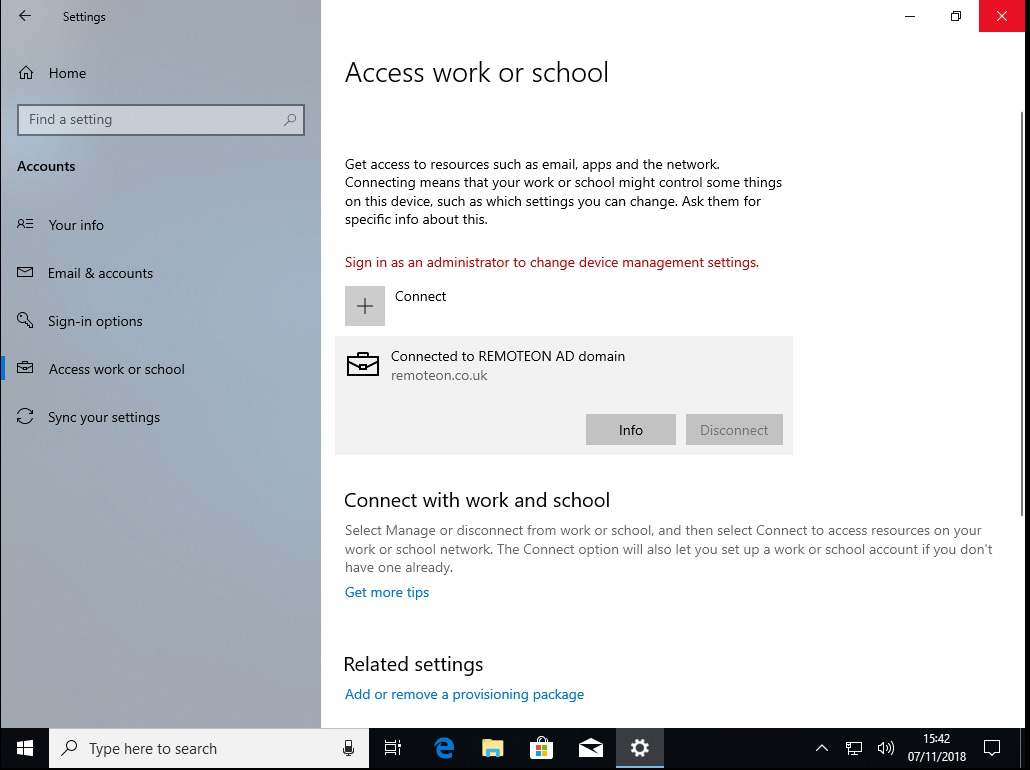
Upon joining it to a network where my DC was I was able to login to the device and access domain resources with no issue. From looking at the state of the machine we can see it joined to my Active Directory domain and also being registered in Intune.
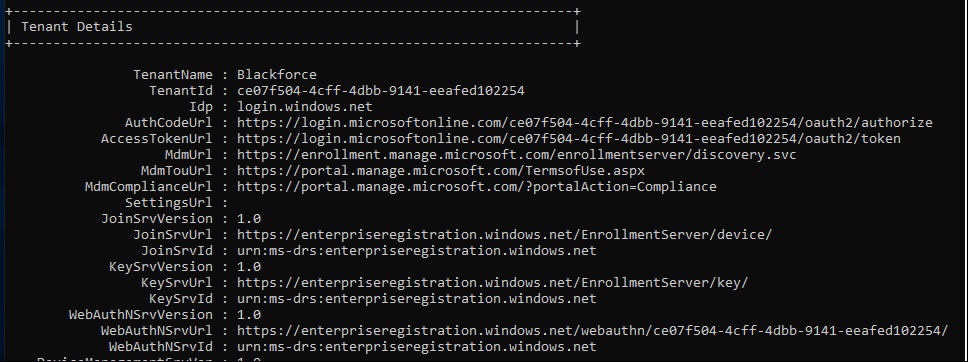
Running a dsreg /status, shows the device also Hybrid Joined to Azure AD.
All done. If the laptop is offsite then it will need to return to base where Active Directory is available. Let me remind you of Microsoft’s pre-req, a VPN is not supported.
- Have access to your Active Directory (VPN connection not supported).
Hopefully one day they will make it so the device is usable before it returns to base as that would be the ultimate dream.